I Stand with Israel – Social Media Poison & Antisemitism
I Stand with Israel
Social Media Poison & Antisemitism
by
Michael Nuccitelli, Psy.D.
October 20, 2023
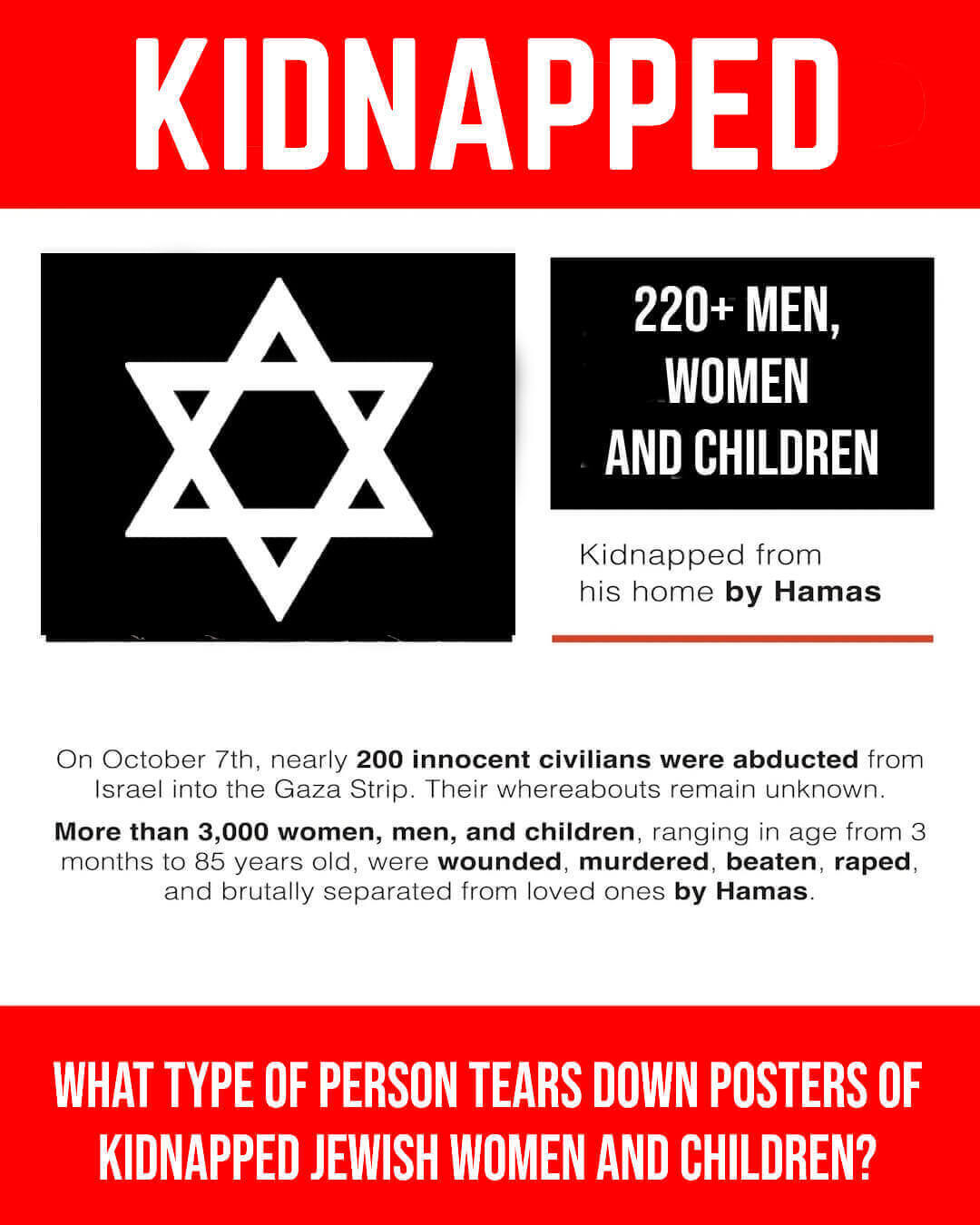
On October 7, 2023, a small piece of humanity died both physically and spiritually. As a clinical psychologist, I have spent a good portion of my life learning about human behavior, criminal psychology, and the dark side of human consciousness. I never imagined I would witness abject evil in my lifetime. 9/11 was horrific but pales in comparison to what happened in Israel. At the time of writing this post, there is a small segment of the population that has been manipulated by what they have seen, heard, and read via social media. We are witnessing how social media has become a dangerous weapon. A prime example of this is watching people tear down the posters of the missing hostages. What type of person would go out of their way to do this? They are not activists, and their actions can be best described as deplorable & pathetic. It may not be illegal, but it is most certainly psychopathic and vicious.
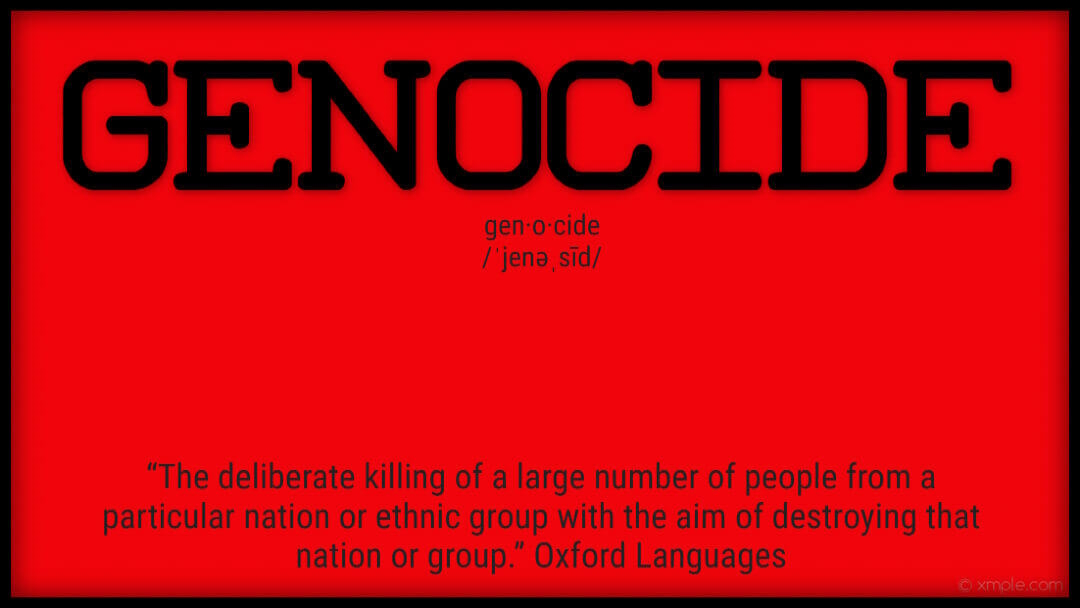
Israel suffered a horrific terrorist attack like the United States did on 9/11. October 7, 2023, has been equated to America’s 9/11 and Pearl Harbor. 1200 men, women and children were brutally murdered, raped, and tortured. 240 hostages are still missing. Israel is being accused of genocide as they seek justice and search for the missing. Americans not only died but are among the missing. The ignorant and angry are protesting without a word about the terrorist attack on Israel. Those who do recognize the attack define it as justified.
Social media has become the main source of information for a growing segment of society. Many young people believe what they see and hear on social media without question. Whether it be artificial intelligence or an orchestrated disinformation campaign, social media is an enemy of Israel. As the Information Age evolves, social media will need to be examined. One of my greatest concerns is that the sanctioning of this mass murder will encourage those living in the United States to do the same. I have a strong suspicion that there will be another terrorist and/or cyber terrorist attack on American soil in the not-too-distant future. Today it is Israel and tomorrow it is?
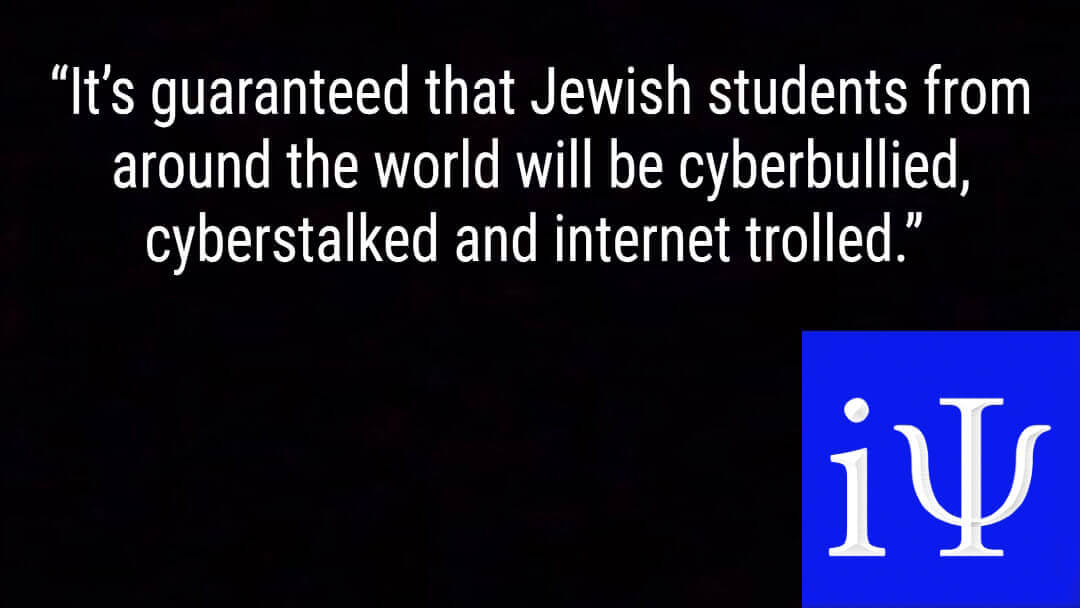
Social media has the capacity to victimize children when it’s cyberbullying and cyberstalking & cyber harassment when it’s adults. Social media now has Israel in its crosshairs. Artificial intelligence and nefarious entities will continue to use social media to manipulate the masses with enormous success. The protests vilifying Israel and the explosion of antisemitism are perfect examples of social media’s capacity to create mass hysteria and to manipulate the uninformed. Social media & the internet have the unique capacity to skew an online user’s perceptions. It is guaranteed that Jewish students will be voraciously cyberbullied, cyberstalked and internet trolled.
If one takes the time to learn about WWII, the holocaust, antisemitism, and the history of the Middle East; it will become clear why Israel is fighting for its very existence. A day will come when it will be proven that the Palestinians wanted Hamas gone. The Palestinians are not Hamas but are unfortunately being used by them for their own malevolent devices. It pains me to watch young Americans and the easily manipulated to be fooled. Social media, disinformation and online deception are the favorite tools used by iPredators and cyber terrorists. Currently, Israel & Jews are the victims.
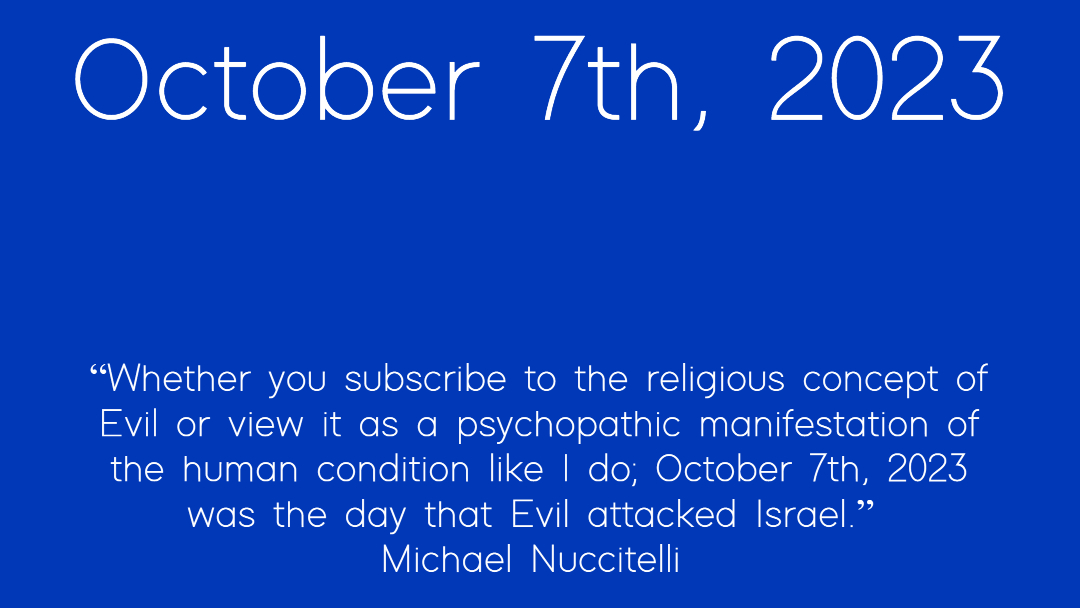
Pasted below are images I’ve created that have been and will be posted throughout my social accounts. They are public domain and free to share and save. Forgive my novice graphic design skills but it is my attempt to support Israel. As a cyberpsychologist who created the iPredator concept over a decade ago and continues to learn about the power of social media, I can safely say that many, many online users both young and old have been seduced by evil. Whether you subscribe to the religious concept of evil or view it as a psychopathic manifestation of the human condition like I do; October 7, 2023, was the day that evil attacked Israel. Social media, the dark side of cyberspace and cyberterrorism are here to stay.
Screams Before Silence Documentary









































Michael Nuccitelli, Psy.D.
Michael Nuccitelli, Psy.D. is a NYS licensed psychologist, cyberpsychologist and online safety educator. In 2009, Dr. Nuccitelli finalized his dark side of cyberspace concept called iPredator. Since 2010, he has advised those seeking information about cyberbullying, cyberstalking, cybercriminal minds, internet addiction and his Dark Psychology concept. By day Dr. Nuccitelli is a practicing psychologist, clinical supervisor and owner of MN Psychological Services, PLLC. After work and on the weekends, he volunteers helping online users who have been cyber-attacked. Dr. Nuccitelli’s is always available to interested parties and the media at no cost. This website and everything created by Dr. Nuccitelli is educational, free and public domain.